Hey and welcome to our new blog. Last week the team participated in the Cyber Grabs 0X03 Junior CTF which was a 12 Hours Jeopardy style team CTF
| CTF | Cyber Grabs 0X03 Junior CTF |
|---|---|
| CTF Start Time | Sun, 06 Feb. 2022, 07:30 EAT |
| CTF End Time | Sun, 06 Feb. 2022, 19:30 EAT |
| CTF Time Event | link |
| Team | Fr334aks-Mini |
| Players | 05t3, Winter, ★sW33t_1mPur1t13s, _k0imet, n3rd, Parsz |
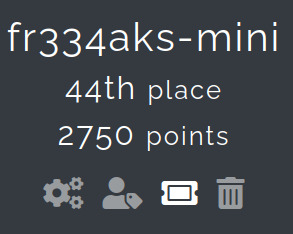
We managed to solve 21/29 challenges where we emerged 44/285 teams with 2750 points. In general, the challenges were fun despite a few challenges with the Infra.
OSINT
Misc
Reverse
Forensic
Mr Robot
Mr. Robot most famous TV show but least people know about it.
Solved by 05t3
We are presented with a .wav file and the first thing that comes to my mind is using Audacity & Sonic Visualizer to check if the flag is visible on the spectogram. Turns out that was a dead end. After sometime of research, i came across a tool on github that could get the flag, stegolsb. To install it, simply run:
1
2
3
git clone https://github.com/ragibson/Steganography
cd Steganography
python3 setup.py install
stegolsb wavsteg -r -i sound_steg.wav -o output.txt -n 1 -b 1000
Breaking down the command above:
- WavSteg uses least significant bit steganography to hide a file in the samples of a .wav file.
-r- is for recovering data from a sound file.-i- Path to a .wav file.-o- Path to an output file.-n- lsb-count (How many LSBs to use [default: 2])-b- How many bytes to recover from the sound file
For more information on stego-lsb, check out the official project description.
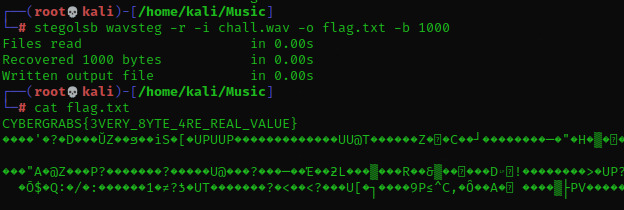
FLAG: CYBERGRABS{3VERY_8YTE_4RE_REAL_VALUE}
